Solution summary
Suggest editsHashicorp Vault is an identity-based secrets and encryption management system. Used with EDB Postgres Advanced Server versions 15.2 and later or EDB Postgres Extended Server versions 15.2 and later, it allows you to control access to encryption keys and certificates and perform key management. Using Hashicorp Vault’s transit secrets engine allows Vault to handle cryptographic functions on data in transit. Hashicorp Vault transit secrets engine can be referred to as "encryption as a service."
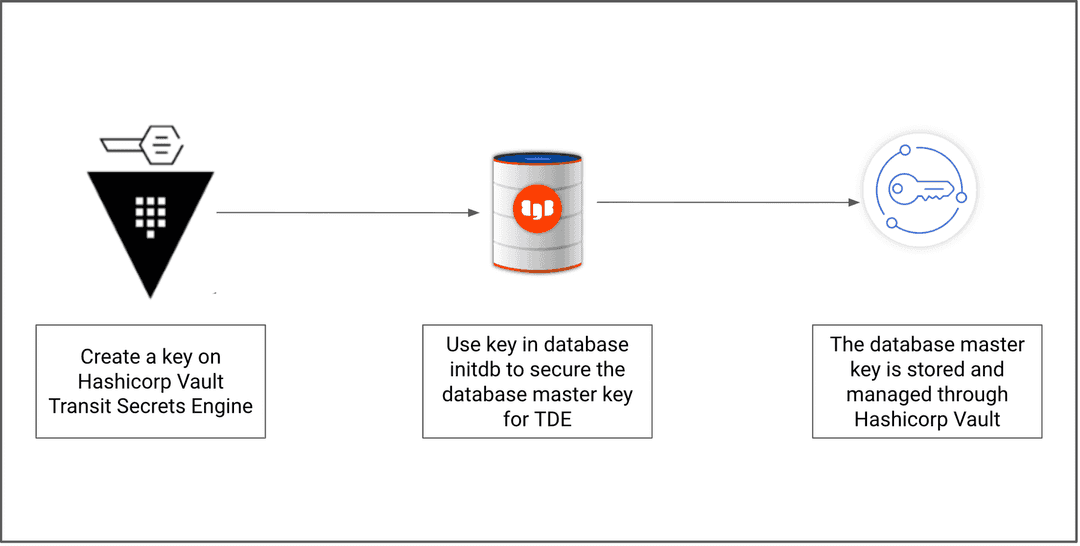
Hashicorp Vault’s primary use case for transit secrets engine is to encrypt data from applications while simultaneously storing encrypted data in some primary data store. Hashicorp Vault transit secrets engine can also generate hashes, sign and verify data, and generate HMACs of data. Hashicorp Vault transit secrets engine can work with EDB Postgres Advanced Server and EDB Postgres Extended Server by securely storing the data key that's generated by initdb. Normally the key, which lives in pg_encryption/key.bin, is stored in plaintext format. However, using Hashicorp Vault transit secrets engine as an external key store manages the data encryption key and provides further security to the key.
The image shows how Hashicorp Vault transit secrets engine works to encrypt and decrypt data.
Could this page be better? Report a problem or suggest an addition!