Next up in our Integrating PostgreSQL blog series, we'll further explore PostgreSQL integration to help enterprises do more and go faster.
This blog post will highlight the next area of importance: Security Integration.
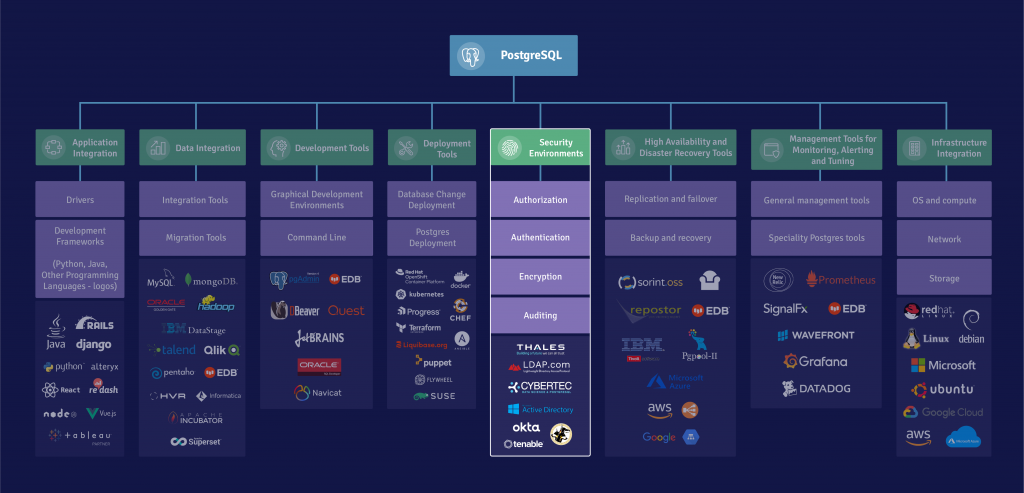
Security Integration
PostgreSQL security should be seen in the context of the data center or cloud. In both cases, the security of the database needs to be part of a Defense in Depth (DiD) concept. For Cloud Native PostgreSQL based on Kubernetes, the 4C model (Cloud, Cluster, Container, Code) model is the emerging best practice. For PostgreSQL deployments in a data center, the best practice for a DiD is discussed in this whitepaper about Security Best Practices for PostgreSQL.
Within PostgreSQL, you need to consider Authentication, Authorization, Auditing, and Encryption.
For authentication, PostgreSQL can define users and passwords inside the database. In that case, we recommend using SCRAM authentication to protect the passwords and forgo the less secure MD5 method. If you use locally defined users and passwords, we recommend EDB PostgreSQL password profiles, which allow you to define expiration, complexity, and reuse rules.
Authorization is handled inside the PostgreSQL database, using roles (i.e., term regrouping users and groups) and attributes, such as LOGIN, SUPERUSER, and so on, that are used when defining privileges.
Separate audit logging is highly valued in environments with elevated compliance requirements, such as financial services. Standard PostgreSQL does not separate the audit log and the system log. EDB’s Postgres Advanced Server provides a separate audit log, with different levels of logging for DDL, DML, or SELECT operations by object type.
Authentication, authorization, and auditing best practices for PostgreSQL are extensively discussed in this blog.
Authentication, authorization, auditing, and encryptions should always be considered together and used with a least-privilege approach.
Stay tuned for the next post in this series, which will cover High Availability and Disaster Recovery tools. In the meantime, check out our infographic to see the bigger picture in regard to PostgreSQL integration.
